Imagine if, in an instant, all the files on your computer vanished, along with all your e-mails and online backups, and therefore any chance of getting those files back. That’s what happened to tech writer Mat Honan, after a hacker broke into his Google and Apple accounts and wiped them clean.
Honan walks through his hacking horror story in painful detail at Wired.com. He describes how his attacker tricked Amazon into revealing the last four digits of his credit card–a key bit of info the hacker needed to gain entry to Honan’s Apple account. Because his Apple e-mail address was on file with Google as a backup, the hacker used it to reset Honan’s Gmail password, which finally let the hacker reset Honan’s Twitter account and achieve the end-goal of taking it over.
In many ways, the hack was preventable. Amazon could have better safeguarded Honan’s credit card details, and Apple could have required more than just a billing address, e-mail address and partial credit card information before resetting Honan’s iCloud account password. Honan could have backed up his files to an external hard drive, or used two-step Gmail authentication to keep the hacker out.
(MORE: 10 Ways to Protect Yourself Online)
But there’s a bigger problem that Honan’s hack brings to light, and that’s how broken the username/password system has become. Every online service we use invites another security threat–a way for hackers to sniff out passwords or glean the information they need to reset an account elsewhere. As Honan himself notes:
My experience leads me to believe that cloud-based systems need fundamentally different security measures. Password-based security mechanisms — which can be cracked, reset, and socially engineered — no longer suffice in the era of cloud computing.
Even if you lock down your Google account with two-step authentication, and Apple and Amazon fix their weak points, there’s no guarantee another service won’t fail, especially when all of them are set up to accommodate forgotten passwords with forgiving recovery mechanisms. What we really need is a new way of verifying our identities online that doesn’t involve memorizing dozens of alphanumeric combinations, and doesn’t add layers of complexity for users.
Slowly, the tech world is coming around to this idea. Tim Bray, who previously worked as Google’s Android developer advocate, recently switched positions within the company to tackle online identity. “Usernames and passwords generally suck and obviously don’t scale to the Internet, so we need to do away with ’em soonest,” Bray wrote in a blog post. In response, Daring Fireball’s John Gruber called online identity “one of the big problems to be solved for the industry over the next decade.”
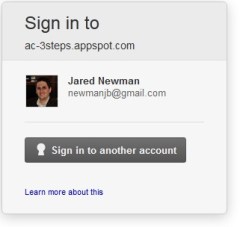 Work is already underway. The OpenID Foundation is coming out with an open source project called Account Chooser, which lets you use a trusted service such as Google to log into other sites. Although Facebook, Twitter and even OpenID already offer this type of universal login, Account Chooser, which was mainly developed by Google, aims to make it more inviting. Instead of seeing the typical login and password fields when you’re signing in at a new site, with Account Chooser you’ll see a slick-looking box that lists your trusted accounts, and all you do is click on the account name to sign in.
Work is already underway. The OpenID Foundation is coming out with an open source project called Account Chooser, which lets you use a trusted service such as Google to log into other sites. Although Facebook, Twitter and even OpenID already offer this type of universal login, Account Chooser, which was mainly developed by Google, aims to make it more inviting. Instead of seeing the typical login and password fields when you’re signing in at a new site, with Account Chooser you’ll see a slick-looking box that lists your trusted accounts, and all you do is click on the account name to sign in.
“It takes the username and password and retires it once and for all,” Don Thibeau, OpenID’s executive director, said in an interview. He hopes to see Account Chooser implemented by the end of the year. Of course, it’s unclear how many websites will adopt it, and how quickly.
But even that’s not a complete solution, since it relies on a master login for Google or whatever other service is providing the credentials. OpenID hopes people will secure their master accounts with two-step authentication, but we should assume most people won’t. (After all, we live in a society where “password” is the most common password.)
That’s why we need better, more effortless ways to lock down our accounts. How this should happen, exactly, is where things get tricky.
OneID, a service that’s in private beta now, also wants to have a single login button that’s ubiquitous across the web, but instead of relying on other trusted accounts like OpenID, it requires users to authenticate their individual devices. That way, no one can access your accounts without physically stealing your computer.
As an added security measure for banking and other important transactions, OneID can require users to enter a PIN on their smartphones through a companion app. As with OpenID, the challenge lies in getting web developers on board, but that may prove even tougher for OneID since it’s just a startup and not a well-known non-profit like OpenID.
Meanwhile, the World Wide Web Consortium has also been brainstorming industry-standard ways to verify users’ identities without endless usernames and passwords. One idea would be to authenticate the browser or device–maybe with a password, or maybe with something fancier, like voice or video recognition–which would then verify your identity with all other web services. That sounds simple enough, but there are lots of details to work out, including what cryptography to use and how to deal with privacy concerns. Web standards tend to take time, but the end result could be widespread adoption of simpler, safer logins.
Jim Fenton, OneID’s chief scientist, believes that individual efforts (such as those of his company) will lead the way, but doesn’t think the username and password are going away anytime soon. “It’s a technology that’s been around for 50 years, and it’s had a chance to establish itself very well on the web,” he said. “I think it will still be quite a while yet.”
Even with a major overhaul in how we identify ourselves online, hackers may still find workarounds. But in time, we may be able to enjoy a system that’s more convenient for everyone–and less prone to horror stories for the unfortunate few.

